VP5500: Unterschied zwischen den Versionen
(++hwinfo) |
D2ns (Diskussion | Beiträge) Keine Bearbeitungszusammenfassung |
||
| (66 dazwischenliegende Versionen von 18 Benutzern werden nicht angezeigt) | |||
| Zeile 1: | Zeile 1: | ||
{{ProjektInfoBox | |||
|name=VP5500 | |||
|status=unknown | |||
|image=Vp5500_full.jpg | |||
|description=Experiments with Philips VP5500 (WLAN VOIP- & Video Phone) | |||
|tags=Software, Telekommunikation, Telefon, | |||
}} | |||
[[Bild:Vp5500_full.jpg|thumb|100px|right|The VP5500 booting]]The Philips VP5500 is a WLAN VOIP- & Video Phone sold by KPN in the netherlands. Some of the features, such as configuration settings for the VOIP connection are usually hidden from the user, but can be revealed through a fake firmware image ([http://spritesmods.com/?art=vpx500 description here]). Thanks to this restriction the device was rendered useless when KPN decided to disconnect the VOIP services this phone was relieing on. | |||
This article intends to collect all relevant information about the hard- & software on the telephone and to provide information to actually reuse the hardware. | |||
== Hardware == | == Hardware == | ||
* | * CPU: [http://www.freescale.com/files/32bit/doc/data_sheet/MC9328MX21.pdf MC9328MX21] @ 266MHz (ARM9 Core) | ||
* FS455LF: PAL Video converter chip | * FS455LF: PAL Video converter chip | ||
* Wlan: Marvell 88w8385 ([http://wireless.kernel.org/en/users/Drivers/libertas OSS driver], [http://www.mikrocontroller.net/attachment/72802/WM-G-MR-01-v27__01192006.pdf | * Wlan: Marvell 88w8385 ([http://wireless.kernel.org/en/users/Drivers/libertas OSS driver], [http://www.mikrocontroller.net/attachment/72802/WM-G-MR-01-v27__01192006.pdf Datasheet]) | ||
* RAM: 64MB (2x K4S56163LF) | * RAM: 64MB (2x K4S56163LF) | ||
* Flash: 16MB | * Flash: 16MB | ||
* Display: 176x220, Samsung LTS220Q1 | |||
* Kamera: Chicony dc-4626.a5 | * Kamera: Chicony dc-4626.a5 | ||
* Audio Codec: [http://focus.ti.com/general/docs/lit/getliterature.tsp?genericPartNumber=tlv320aic12k&fileType=pdf TI TLV 320 AIC 12K] | |||
=== VP6500 Ladeschaltung === | |||
* Texas Instruments BQ22400 Lade IC | |||
* Philips PMWD20XN Mosfet | |||
Die Ladeschaltung ist extrem Akku-schädlich: Der Lade-IC wird ohne Temperatursensor verwendet, und hat keine Delta-Peak abschaltung. Als Abschaltungsmodi bleiben also nur die Absolutspannung und ein Ladetimer. Da man eigentlich NiMH-Akkus nicht mit reiner Spannungsabschaltung laden kann (was hat TI da geritten?!?) bleibt also nur der Lade-timer. Wenn man das Telefon in die Ladeschale stellt beginnt es jedes mal einen neuen Ladezyklus (der Prozessor hat da keinen Einfluss drauf, der Lade-IC macht das halt so). Dadurch werden die Akkus jedes mal extrem überladen (nur der timer schaltet ab), und haben eine kurze Lebensdauer. | |||
== | Workarounds: | ||
=== | * Das Telefon nur in die Ladeschale stellen, wenn es anfängt, sich über den leeren Akku zu beschweren. | ||
* Thermistor nach Datenblatt des ICs dazu fummeln (ziemlich aufwändig, alleine das Außeinanderbauen des dummen Phones ist der totale Krampf). Ich hab das aber jetzt mal gemacht. Ich hab zwischen Pins 5 und 7 des ICs einen 18k-Widerstand hinzugefügt, und eine Thermistor zwischen GND und Pin5, den ich aus nem Notebookakku ausgeschlachtet habe. Mal sehen ob es funktioniert. | |||
*Die Ladeschaltung totlegen (die untere Induktivität auf der Platine auslöten sollte reichen, habe ich allerdings nicht ausprobiert), und die Akkus wenn sie wirklich leer sind in einem normalen Ladegerät laden. Eine kleine Erhaltungladung bekommen sie im VP6500 trotzdem wegen eines 150-Ohm Widerstands zwischen +5V und Akku+. Auf die Art kann man das Telefon in die Ladeschale stellen ohne die Akkus zu zerstören. | |||
=== GPIO Interfaces === | |||
The script '''/usr/local/tmp/HD1_ats.sh''' is a test script for the developers. This script contains a lot of information about how to control peripheral devices of the phone (such as backlight). | |||
The VP6500 has '''/user_data/prod/HC1V00_ats.sh''' instead (and symlinks '''HC1_ats.sh''' and '''prod_ats.sh''' in the same directory). | |||
* [[VP5500/GPIO_backlight]] | |||
== Pinning == | |||
=== Serial === | |||
[[Bild:Vp5500_serial.jpg|thumb|120px|right|serial pins beneath the battery]] | |||
[[Bild:Vp5500_serial.png]] | [[Bild:Vp5500_serial.png]] | ||
VCC: 3.3V | VCC: 3.3V, Rate 115200 Baud | ||
* Step 1 | |||
Connect a serial USB uart as shown above. | |||
* Step 2 | |||
Set TIN pin low state. | |||
* Step 3 | |||
Use any terminal programm to see the kernel bootlog. | |||
You should see: | |||
imx21 login: | |||
But you don't know the login. | |||
* Step 4 | |||
Shutdown the phone. | |||
* Step 5 | |||
The bootloader stops as soons as it sees characters on the UART interface. | |||
Pressing buttons on the phone doesn't work ! | |||
Hit your keyboard and press the power button on the phone. | |||
You should see the bootloader console: | |||
blob> | |||
Fortunately the bootloader allows editing the kernel command line, so you're able to directly "chroot" the device by setting a different initrc (sh). | |||
* Step 6 | |||
Type the following at the bootloader prompt: | |||
boot root=/dev/mtdblock2 init=/bin/sh | boot root=/dev/mtdblock2 init=/bin/sh | ||
[[VP5500/bootlog|Boot Log]] | * [[VP5500/bootlog|Boot Log]] of the standard installation | ||
== | * [[VP5500/serial howto|How to add a serial interface to your device]] | ||
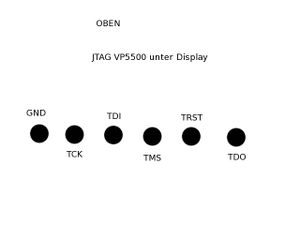
=== JTAG === | |||
[[Bild:Vp5500_jtag.jpg|rahmenlos]] | |||
Pins are at the back of the circuit board. | |||
== Partitions == | |||
0x00000000-0x00014000 : "bootloader" blob version 2.0.5-pre2 | 0x00000000-0x00014000 : "bootloader" blob version 2.0.5-pre2 | ||
0x00014000-0x00100000 : "kernel" | 0x00014000-0x00100000 : "kernel" /boot (?) | ||
0x00100000-0x01ce0000 : "fs #1" | 0x00100000-0x01ce0000 : "fs #1" / | ||
0x01ce0000-0x01fe0000 : "fs #2" | 0x01ce0000-0x01fe0000 : "fs #2" /user_data | ||
0x01fe0000-0x02000000 : "fs #3" | 0x01fe0000-0x02000000 : "fs #3" /user_settings | ||
== | ==Drivers & Software== | ||
===Audio=== | ===Audio=== | ||
* | * Looks as if the audio codec in use needs a proprietary driver | ||
==== Sound files ==== | |||
The sound files can be found in /usr/local/etc/SystemRingTones/ and are mono wave files with a sample rate of 16khz | |||
===MPEG en/decoder=== | ===MPEG en/decoder=== | ||
* Hantrop MPEG EN- DECODER, kernel | * Hantrop MPEG EN- DECODER, kernel module: hmp4e | ||
=== | ===Camera=== | ||
* [http://www.bitshrine.org/gpp/celinux-040503-mw-v4l2-1.patch Patch | * [http://www.bitshrine.org/gpp/celinux-040503-mw-v4l2-1.patch Patch for 2.4.X] - CMOS Sensor connected via I²C | ||
===Wlan=== | ===Wlan=== | ||
* [http://wireless.kernel.org/en/users/Drivers/libertas Libertas OSS driver] | * [http://wireless.kernel.org/en/users/Drivers/libertas Libertas OSS driver] | ||
===Framebuffer=== | |||
[[Bild:Example_bootlogo.png|thumb|100px|right|This shows an example of the visible (white are w/ logo) vs. virtual (striped) framebuffer size]] | |||
Although the display is 176x220, the framebuffer has a virtual size of 240x220 pixels. | |||
====Creating an own splash image==== | |||
* Create an image with 240x220 pixels in size | |||
** Note: The on-screen visible area of this image is in the upper left corner with a size of 176x220 (actual display size). Furthermore the image is flipped upside down. | |||
* Save it as RGB565 Bitmap (=5b for R, 6b for G, 5b for B) (gimp can do this for you) | |||
* Strip off the BMP header: | |||
tail -c 105600 your_bitmap.bmp > your_splasimage.bin | |||
* Copy your shiny new splash image to /user_data/data/welcome.rgb565 | |||
====2nd Splash image==== | |||
[[Bild:Example_bootlogo.gif|right|thumb|80px|Example bootlogo]] | |||
The 2nd image is an animated GIF file and can be found in /usr/local/pics/qpe/splash.gif | |||
====Direct drawing to framebuffer==== | |||
Drawing to framebuffer in C is quite easy. Open /dev/fb and create a mmap on it. Then cast the pointer to short: | |||
int fb_nr = open("/dev/fb", O_RDWR); | |||
void* fb_void = mmap(0, 2*240*220, PROT_WRITE, MAP_SHARED , fb_nr, 0); | |||
short* fb = (short*) fb_void; | |||
Then you can simply access every Pixel via <code>fb[240 * y + x]</code>. The packing is the same (rgb565) as described above. | |||
===Buttons=== | |||
The buttons are accessable via /dev/buttons. While you open this device qtopia does not handle Input at the same time. Each key-event results in byte from /dev/buttons. One on pressing (make-code) and one on releasing (break-code) the button. The break-code is always <code>make + 0x80</code>. Here is a list of the make-codes: | |||
{| | |||
! Button !! make | |||
|- | |||
| left action || 0x7c | |||
|- | |||
| right action || 0x42 | |||
|- | |||
| OK || 0x74 | |||
|- | |||
| left || 0x69 | |||
|- | |||
| right || 0x6a | |||
|- | |||
| up || 0x67 | |||
|- | |||
| down || 0x6c | |||
|- | |||
| pick up || 0x57 | |||
|- | |||
| hang up || 0x58 | |||
|- | |||
| numpad n || 0x01 +n | |||
|- | |||
| numpad * || 0x37 | |||
|- | |||
| numpad 0 || 0x0b | |||
|- | |||
| numpad # || 0x54 | |||
|- | |||
| video || 0x40 | |||
|- | |||
| magnify || 0x5a | |||
|} | |||
== Software == | |||
=== GPL-Sources (incomplete) === | |||
* [http://dn.fqdn.org/vpx500/VP5500-6500.zip VP5500-6500.zip] | |||
=== Bootloader (Blob) === | |||
* [http://www.lartmaker.nl/lartware/blob/ Project download page] | |||
=== Root FS & Toolchain === | |||
According to the boot log, the root fs is derived from some sample source code for the [http://www.freescale.com/webapp/search/Serp.jsp?QueryText=&fsrch=1&sessionChecker=&attempt=1&showCustomCollateral=false&RELEVANCE=true&fromTrng=false&showAllCategories=false&isResult=false&Product+Type=Products%2F040M934302706246%60%60Microcontrollers+and+Processors%2F002M0yls8rH3%60%6032-Bit+Microcontrollers+%26+Processors%2F0011117821752551713721143%60%60ARM+Based%2F010M0ylsZrDR%60%60i.MX+Applications+Processors%2F010KFP1CPN6U%60%60i.MX21+Family%2F&isFromFlex=false&isTree=false&pageSize=25&fromASP=false&isAdvanceSearch=false&fromPSP=false&SelectedAsset=Design+Tools&iteration=1&pageNum=1&assetLocked=false&assetLockedForNavigation=false&fromCust=false&fromDAP=false&fromWebPages=false&isComparison=false iMX21 development platform]. | |||
* [[VP5500/ps output|process list]] | |||
* [http://downloads.openmoko.org/developer/toolchains/ pre-built toolchains] | |||
=== Kernel === | |||
Version: 2.4.20 | |||
* [[VP5500/modules|modules in use]] | |||
=== Misc === | |||
To run the applications in /usr/local/bin, run '''export QTDIR=/usr/local''' first. | |||
=== Boot process === | |||
Scripts & programs run at boot time: | |||
* /etc/rc.d/rcS | |||
* /etc/rc.d/init.d/* | |||
* /usr/local/startup/daemon.sh (invoked by inittab) | |||
** qpe | |||
** upgraded | |||
** netsyncd | |||
== Networking stuff == | |||
WPA Settings can be configured by editing the file '''/etc/marvell/wpa_supplicant.conf''' and '''/etc/marvell/iwconfig''' (vi is installed).<br> | |||
'''Important: All lines have two withspaces in front of it ! Using a different whitespace count will not work !''' | |||
Example wpa_supplicant.conf: | |||
network={ | |||
ssid="your_ssid" | |||
scan_ssid=1 | |||
proto=WPA | |||
key_mgmt=WPA-PSK | |||
pairwise=TKIP | |||
group=TKIP | |||
psk="your_passphrase" | |||
} | |||
After altering wpa_supplicant.conf, you'll need to set the correct value for the '''ssid''' field in '''/etc/marvell/iwconfig'''. | |||
The default configuration restricts WPA Supplicant to operate only in WPA1 mode. WPA2 can be enabled by changing the configuration as follows: | |||
network={ | |||
ssid="your_ssid" | |||
scan_ssid=1 | |||
#proto=WPA | |||
key_mgmt=WPA-PSK | |||
#pairwise=TKIP | |||
#group=TKIP | |||
psk="your_passphrase" | |||
} | |||
'''Note:''' After above changes are applied, the "registration" application will behave a little different: It'll always prompt a list with wifi networks, asking you to select one. If you select the default choice (which is the one you set up in wpa_supplicant.conf), the registration application tries to be "smart" and will disable the WPA option. | |||
In order to enable the WPA option again, do not choose your essid, but select the option "Add Wifi Network" and type the name of your network, then select "WPA". | |||
== Configuration == | |||
'''For Sipgate:''' | |||
'''SIP1''' | |||
Display Name: your Name | |||
User Name: your SIP-ID | |||
Telephone Number: Tel.Nr. | |||
'''Auth''' | |||
Authentification UserName: your SIP-ID | |||
Password: Sipgate Password | |||
'''Server''' | |||
SIP register address:port: sipgate.de:5060 | |||
'''Proxy''' | |||
SIP proxy1 address:port: sipgate.de:5060 | |||
'''SIP2''' | |||
SIP Port Listen | |||
for UDP: 5062 | |||
for TCP: 5062 | |||
for TCP TLS: 5053 | |||
'''STUN''' | |||
[X] use rport | |||
SIP Outbound needs to be empty. | |||
=== 30-second bug === | |||
In some setups the phone will send a SIP BYE message and terminate an incoming call after 30 seconds for some reason - presumably because it expects some special message from the SIP Server. | |||
You need to edit '''/user_data/data/hpr0userparam.cfg''' and set the value of '''OPTIONS_KEEP_ALIVE''' to '''0'''. | |||
== | == Making Backups == | ||
If you want to make a backup of your root partition, you can do as follows: | |||
echo '#!/bin/sh' > /tmp/backup.sh | |||
echo 'cat /dev/mtdb2' >> /tmp/backup.sh | |||
chmod 700 /tmp/backup.sh | |||
micro_inetd 31337 /tmp/backup.sh | |||
This'll make your device listen for incoming connections on port 31337. On your host system you may then simply run "nc ip.of.your.phone 31337 > /path/to/backup/file" - et voilà, you got your rootfs packed into a file. Note that the backed up file is not ext2, but a jffs2 formatted filesystem. These can't be handled by a simple "mount -o loop" as you'd have thought... so here's how you mount it: | |||
modprobe jffs2 | |||
modprobe mtdram total_size=32768 erase_size=128 | |||
modprobe mtdblock | |||
mkdir /tmp/phone-root | |||
mknod /tmp/phone-mtdb2 b 31 0 | |||
dd if=/your/backup/file of=/tmp/phone-mtdb2 | |||
mount -t jffs2 /tmp/phone-mtdb2 /tmp/phone-root | |||
This was easy, wasn't it? ;) | |||
=Malfunctions on VP6500= | |||
== Red light of death == | |||
===Symptoms=== | |||
* Flashing Keypad for a few seconds (2-3 times) | |||
* Red constant camera light | |||
* NOTHING | |||
= Links = | |||
* [http://www.mikrocontroller.net/topic/170483 Thread where the actual reverse engineering happens] | |||
* Results will be demonstrated on the workshop [[Workshop_root_your_toaster|root your toaster]] (2010/05/01) | |||
* [http://spritesmods.com/?art=vpx500 Hack to reveal the Config interface] | |||
* [http://www.mikrocontroller.net/articles/PHILIPS_VP5500_VoIP_Telefon some more information] | |||
* [http://vp6500.bd8.nl/ Binary packages for the VP'''6'''500 (most of it should be compatible)] | |||
* [http://www.imxdev.org/wiki/index.php?title=All Tips & Tricks for the MX21 devboard] | |||
* [http://www.ailis.de/~k/archives/19-ARM-cross-compiling-howto.html Cross compile howto] | |||
Aktuelle Version vom 8. April 2017, 21:53 Uhr
| VP5500 Release status: unknown [box doku] | |
|---|---|

| |
| Description | Experiments with Philips VP5500 (WLAN VOIP- & Video Phone) |
The Philips VP5500 is a WLAN VOIP- & Video Phone sold by KPN in the netherlands. Some of the features, such as configuration settings for the VOIP connection are usually hidden from the user, but can be revealed through a fake firmware image (description here). Thanks to this restriction the device was rendered useless when KPN decided to disconnect the VOIP services this phone was relieing on.
This article intends to collect all relevant information about the hard- & software on the telephone and to provide information to actually reuse the hardware.
Hardware[Bearbeiten | Quelltext bearbeiten]
- CPU: MC9328MX21 @ 266MHz (ARM9 Core)
- FS455LF: PAL Video converter chip
- Wlan: Marvell 88w8385 (OSS driver, Datasheet)
- RAM: 64MB (2x K4S56163LF)
- Flash: 16MB
- Display: 176x220, Samsung LTS220Q1
- Kamera: Chicony dc-4626.a5
- Audio Codec: TI TLV 320 AIC 12K
VP6500 Ladeschaltung[Bearbeiten | Quelltext bearbeiten]
- Texas Instruments BQ22400 Lade IC
- Philips PMWD20XN Mosfet
Die Ladeschaltung ist extrem Akku-schädlich: Der Lade-IC wird ohne Temperatursensor verwendet, und hat keine Delta-Peak abschaltung. Als Abschaltungsmodi bleiben also nur die Absolutspannung und ein Ladetimer. Da man eigentlich NiMH-Akkus nicht mit reiner Spannungsabschaltung laden kann (was hat TI da geritten?!?) bleibt also nur der Lade-timer. Wenn man das Telefon in die Ladeschale stellt beginnt es jedes mal einen neuen Ladezyklus (der Prozessor hat da keinen Einfluss drauf, der Lade-IC macht das halt so). Dadurch werden die Akkus jedes mal extrem überladen (nur der timer schaltet ab), und haben eine kurze Lebensdauer.
Workarounds:
- Das Telefon nur in die Ladeschale stellen, wenn es anfängt, sich über den leeren Akku zu beschweren.
- Thermistor nach Datenblatt des ICs dazu fummeln (ziemlich aufwändig, alleine das Außeinanderbauen des dummen Phones ist der totale Krampf). Ich hab das aber jetzt mal gemacht. Ich hab zwischen Pins 5 und 7 des ICs einen 18k-Widerstand hinzugefügt, und eine Thermistor zwischen GND und Pin5, den ich aus nem Notebookakku ausgeschlachtet habe. Mal sehen ob es funktioniert.
- Die Ladeschaltung totlegen (die untere Induktivität auf der Platine auslöten sollte reichen, habe ich allerdings nicht ausprobiert), und die Akkus wenn sie wirklich leer sind in einem normalen Ladegerät laden. Eine kleine Erhaltungladung bekommen sie im VP6500 trotzdem wegen eines 150-Ohm Widerstands zwischen +5V und Akku+. Auf die Art kann man das Telefon in die Ladeschale stellen ohne die Akkus zu zerstören.
GPIO Interfaces[Bearbeiten | Quelltext bearbeiten]
The script /usr/local/tmp/HD1_ats.sh is a test script for the developers. This script contains a lot of information about how to control peripheral devices of the phone (such as backlight). The VP6500 has /user_data/prod/HC1V00_ats.sh instead (and symlinks HC1_ats.sh and prod_ats.sh in the same directory).
Pinning[Bearbeiten | Quelltext bearbeiten]
Serial[Bearbeiten | Quelltext bearbeiten]
VCC: 3.3V, Rate 115200 Baud
- Step 1
Connect a serial USB uart as shown above.
- Step 2
Set TIN pin low state.
- Step 3
Use any terminal programm to see the kernel bootlog. You should see:
imx21 login:
But you don't know the login.
- Step 4
Shutdown the phone.
- Step 5
The bootloader stops as soons as it sees characters on the UART interface. Pressing buttons on the phone doesn't work ! Hit your keyboard and press the power button on the phone. You should see the bootloader console:
blob>
Fortunately the bootloader allows editing the kernel command line, so you're able to directly "chroot" the device by setting a different initrc (sh).
- Step 6
Type the following at the bootloader prompt:
boot root=/dev/mtdblock2 init=/bin/sh
- Boot Log of the standard installation
- How to add a serial interface to your device
JTAG[Bearbeiten | Quelltext bearbeiten]
Pins are at the back of the circuit board.
Partitions[Bearbeiten | Quelltext bearbeiten]
0x00000000-0x00014000 : "bootloader" blob version 2.0.5-pre2 0x00014000-0x00100000 : "kernel" /boot (?) 0x00100000-0x01ce0000 : "fs #1" / 0x01ce0000-0x01fe0000 : "fs #2" /user_data 0x01fe0000-0x02000000 : "fs #3" /user_settings
Drivers & Software[Bearbeiten | Quelltext bearbeiten]
Audio[Bearbeiten | Quelltext bearbeiten]
- Looks as if the audio codec in use needs a proprietary driver
Sound files[Bearbeiten | Quelltext bearbeiten]
The sound files can be found in /usr/local/etc/SystemRingTones/ and are mono wave files with a sample rate of 16khz
MPEG en/decoder[Bearbeiten | Quelltext bearbeiten]
- Hantrop MPEG EN- DECODER, kernel module: hmp4e
Camera[Bearbeiten | Quelltext bearbeiten]
- Patch for 2.4.X - CMOS Sensor connected via I²C
Wlan[Bearbeiten | Quelltext bearbeiten]
Framebuffer[Bearbeiten | Quelltext bearbeiten]
Although the display is 176x220, the framebuffer has a virtual size of 240x220 pixels.
Creating an own splash image[Bearbeiten | Quelltext bearbeiten]
- Create an image with 240x220 pixels in size
- Note: The on-screen visible area of this image is in the upper left corner with a size of 176x220 (actual display size). Furthermore the image is flipped upside down.
- Save it as RGB565 Bitmap (=5b for R, 6b for G, 5b for B) (gimp can do this for you)
- Strip off the BMP header:
tail -c 105600 your_bitmap.bmp > your_splasimage.bin
- Copy your shiny new splash image to /user_data/data/welcome.rgb565
2nd Splash image[Bearbeiten | Quelltext bearbeiten]
The 2nd image is an animated GIF file and can be found in /usr/local/pics/qpe/splash.gif
Direct drawing to framebuffer[Bearbeiten | Quelltext bearbeiten]
Drawing to framebuffer in C is quite easy. Open /dev/fb and create a mmap on it. Then cast the pointer to short:
int fb_nr = open("/dev/fb", O_RDWR);
void* fb_void = mmap(0, 2*240*220, PROT_WRITE, MAP_SHARED , fb_nr, 0);
short* fb = (short*) fb_void;
Then you can simply access every Pixel via fb[240 * y + x]. The packing is the same (rgb565) as described above.
Buttons[Bearbeiten | Quelltext bearbeiten]
The buttons are accessable via /dev/buttons. While you open this device qtopia does not handle Input at the same time. Each key-event results in byte from /dev/buttons. One on pressing (make-code) and one on releasing (break-code) the button. The break-code is always make + 0x80. Here is a list of the make-codes:
| Button | make |
|---|---|
| left action | 0x7c |
| right action | 0x42 |
| OK | 0x74 |
| left | 0x69 |
| right | 0x6a |
| up | 0x67 |
| down | 0x6c |
| pick up | 0x57 |
| hang up | 0x58 |
| numpad n | 0x01 +n |
| numpad * | 0x37 |
| numpad 0 | 0x0b |
| numpad # | 0x54 |
| video | 0x40 |
| magnify | 0x5a |
Software[Bearbeiten | Quelltext bearbeiten]
GPL-Sources (incomplete)[Bearbeiten | Quelltext bearbeiten]
Bootloader (Blob)[Bearbeiten | Quelltext bearbeiten]
Root FS & Toolchain[Bearbeiten | Quelltext bearbeiten]
According to the boot log, the root fs is derived from some sample source code for the iMX21 development platform.
Kernel[Bearbeiten | Quelltext bearbeiten]
Version: 2.4.20
Misc[Bearbeiten | Quelltext bearbeiten]
To run the applications in /usr/local/bin, run export QTDIR=/usr/local first.
Boot process[Bearbeiten | Quelltext bearbeiten]
Scripts & programs run at boot time:
- /etc/rc.d/rcS
- /etc/rc.d/init.d/*
- /usr/local/startup/daemon.sh (invoked by inittab)
- qpe
- upgraded
- netsyncd
Networking stuff[Bearbeiten | Quelltext bearbeiten]
WPA Settings can be configured by editing the file /etc/marvell/wpa_supplicant.conf and /etc/marvell/iwconfig (vi is installed).
Important: All lines have two withspaces in front of it ! Using a different whitespace count will not work !
Example wpa_supplicant.conf:
network={
ssid="your_ssid"
scan_ssid=1
proto=WPA
key_mgmt=WPA-PSK
pairwise=TKIP
group=TKIP
psk="your_passphrase"
}
After altering wpa_supplicant.conf, you'll need to set the correct value for the ssid field in /etc/marvell/iwconfig.
The default configuration restricts WPA Supplicant to operate only in WPA1 mode. WPA2 can be enabled by changing the configuration as follows:
network={
ssid="your_ssid"
scan_ssid=1
#proto=WPA
key_mgmt=WPA-PSK
#pairwise=TKIP
#group=TKIP
psk="your_passphrase"
}
Note: After above changes are applied, the "registration" application will behave a little different: It'll always prompt a list with wifi networks, asking you to select one. If you select the default choice (which is the one you set up in wpa_supplicant.conf), the registration application tries to be "smart" and will disable the WPA option.
In order to enable the WPA option again, do not choose your essid, but select the option "Add Wifi Network" and type the name of your network, then select "WPA".
Configuration[Bearbeiten | Quelltext bearbeiten]
For Sipgate:
SIP1
Display Name: your Name
User Name: your SIP-ID
Telephone Number: Tel.Nr.
Auth
Authentification UserName: your SIP-ID
Password: Sipgate Password
Server
SIP register address:port: sipgate.de:5060
Proxy
SIP proxy1 address:port: sipgate.de:5060
SIP2
SIP Port Listen
for UDP: 5062
for TCP: 5062
for TCP TLS: 5053
STUN
[X] use rport
SIP Outbound needs to be empty.
30-second bug[Bearbeiten | Quelltext bearbeiten]
In some setups the phone will send a SIP BYE message and terminate an incoming call after 30 seconds for some reason - presumably because it expects some special message from the SIP Server.
You need to edit /user_data/data/hpr0userparam.cfg and set the value of OPTIONS_KEEP_ALIVE to 0.
Making Backups[Bearbeiten | Quelltext bearbeiten]
If you want to make a backup of your root partition, you can do as follows:
echo '#!/bin/sh' > /tmp/backup.sh echo 'cat /dev/mtdb2' >> /tmp/backup.sh chmod 700 /tmp/backup.sh micro_inetd 31337 /tmp/backup.sh
This'll make your device listen for incoming connections on port 31337. On your host system you may then simply run "nc ip.of.your.phone 31337 > /path/to/backup/file" - et voilà, you got your rootfs packed into a file. Note that the backed up file is not ext2, but a jffs2 formatted filesystem. These can't be handled by a simple "mount -o loop" as you'd have thought... so here's how you mount it:
modprobe jffs2 modprobe mtdram total_size=32768 erase_size=128 modprobe mtdblock mkdir /tmp/phone-root mknod /tmp/phone-mtdb2 b 31 0 dd if=/your/backup/file of=/tmp/phone-mtdb2 mount -t jffs2 /tmp/phone-mtdb2 /tmp/phone-root
This was easy, wasn't it? ;)
Malfunctions on VP6500[Bearbeiten | Quelltext bearbeiten]
Red light of death[Bearbeiten | Quelltext bearbeiten]
Symptoms[Bearbeiten | Quelltext bearbeiten]
- Flashing Keypad for a few seconds (2-3 times)
- Red constant camera light
- NOTHING
Links[Bearbeiten | Quelltext bearbeiten]
- Thread where the actual reverse engineering happens
- Results will be demonstrated on the workshop root your toaster (2010/05/01)
- Hack to reveal the Config interface
- some more information
- Binary packages for the VP6500 (most of it should be compatible)
- Tips & Tricks for the MX21 devboard
- Cross compile howto