DongleExtension: Unterschied zwischen den Versionen
Soeren (Diskussion | Beiträge) K (konzept fuer dongleextextension eingefügt, schaltpläne, code & bilder folgen) |
Sauron (Diskussion | Beiträge) Keine Bearbeitungszusammenfassung |
||
| (4 dazwischenliegende Versionen von 3 Benutzern werden nicht angezeigt) | |||
| Zeile 1: | Zeile 1: | ||
{{ProjektInfoBox | |||
|name = dongleextension | |||
|status = experimental | |||
|image = Dongleextension_principle.png | |||
|description = A USB dongle to keep your secrets | |||
|author = [[Benutzer:Soeren|Soeren]] | |||
|username = | |||
|version = 0.0.0 | |||
|update = | |||
|platform = AVR | |||
|license = GPLv2 or later | |||
|download = | |||
}} | |||
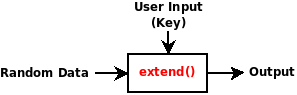
==PRINCIPLE== | ==PRINCIPLE== | ||
[[Bild:Dongleextension_principle.png|left]] | |||
This device was designed for reducing long passphrases to | This device was designed for reducing long passphrases to | ||
rememberable shorter passphrases or even numerical pins. | rememberable shorter passphrases or even numerical pins. | ||
| Zeile 30: | Zeile 45: | ||
is used to assure that the user is present. | is used to assure that the user is present. | ||
===The extend() function=== | |||
The extension function may be any cryptographically secure one-way | |||
function (i.e. a hash function), any cipher function or a combination | |||
of both. | |||
==PROTECTION GOALS== | ==PROTECTION GOALS== | ||
| Zeile 51: | Zeile 70: | ||
agains this kind of attack can't be assured since this always depends | agains this kind of attack can't be assured since this always depends | ||
on the configuration and hardware design of the host system. | on the configuration and hardware design of the host system. | ||
This attack may also be viable on setups where a smartcard is used if | |||
the attacker is able to eavesdrop the communication between the operating | |||
system and the smartcard. | |||
===Overclocking=== | ===Overclocking=== | ||
| Zeile 56: | Zeile 79: | ||
the delay between two extension cycles and therefore may the be able | the delay between two extension cycles and therefore may the be able | ||
to speed up brute force probing of the key. | to speed up brute force probing of the key. | ||
Note: The attacker does not gain any knowledge about the secret stored on | |||
the dongle extension. | |||
===Replacing parts of the initrd=== | ===Replacing parts of the initrd=== | ||
| Zeile 61: | Zeile 87: | ||
passphrase to the usb device. This or other software within the | passphrase to the usb device. This or other software within the | ||
initrd image on your system can be replaced by a malicious attacker. | initrd image on your system can be replaced by a malicious attacker. | ||
Usually this can be done by any user that has root | Usually this can be done by any user that has root privileges on | ||
your system. | your system. | ||
Note: This attack is an essential problem with harddisk encryption nowadays. An | |||
attacker that is able to replace your bootloader, kernel, initrd or bios | |||
will be able to recover your encryption passphrase. | |||
==HARDWARE== | ==HARDWARE== | ||
This device basically consists of an Atmega8 microcontroller, | This device basically consists of an Atmega8 microcontroller, | ||
a push button | a push button and a dual-color (red/green) led. When the device | ||
is plugged in, it announces itself as an hid keyboard to the | is plugged in, it announces itself as an hid keyboard to the | ||
host system. When plugged it, it waits for a configurable amount of | host system. When plugged it, it waits for a configurable amount of | ||
| Zeile 81: | Zeile 110: | ||
the input is fed to the extension function, processed and sent as | the input is fed to the extension function, processed and sent as | ||
"keystrokes" to the host system. | "keystrokes" to the host system. | ||
<!-- keine Inhalte nach diesem Kommentar! (Fuß-Banner) --> | |||
{{Ueberarbeitungsbedarf|grund=Auf diese Seite wird nirgends verlinkt}} | |||
Aktuelle Version vom 11. Januar 2010, 00:20 Uhr
| dongleextension Release status: experimental [box doku] | |
|---|---|
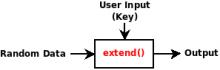
| |
| Description | A USB dongle to keep your secrets |
| Author(s) | Soeren |
| Last Version | 0.0.0 () |
| Platform | AVR |
| License | GPLv2 or later |
PRINCIPLE[Bearbeiten | Quelltext bearbeiten]
This device was designed for reducing long passphrases to rememberable shorter passphrases or even numerical pins. It can be of aid for harddisk encryption: i.e. long passphrases are reduced to a shorter secret. This device may not be an adequate replacement for a smartcard (read the "attacks" section below) - in fact a smartcard may be an even better choice when you want to protect against an attacker that does differential power analysis.
This device emulates the function of a smartcard: It holds an encrypted secret that is decrypted with the correct passphrase. In contrast to smartcards, the device does not know what the correct key or secret is. It therefore can't distinguish between correct and incorrect input, thus there is no self-locking mechanism that disables the device when a number of failed attempts to unlock have been made.
For protection against brute force attacks, the device waits for a configurable delay and does give no feedback as to whether the decrypted result is correct or not. The wait cycle is executed upon startup and not after a certain input has been given. The idea behind is the following: The device is usually plugged in at boot time (whenever you turn on the computer). Bios and bootloader usually need some time to initialize anyway, so this delay may (depending on the configuration) not even be noticeable by the user.
The device also has a push button attached to it. This button is used to assure that the user is present.
The extend() function[Bearbeiten | Quelltext bearbeiten]
The extension function may be any cryptographically secure one-way function (i.e. a hash function), any cipher function or a combination of both.
PROTECTION GOALS[Bearbeiten | Quelltext bearbeiten]
The device itself contains chunks of random data plus firmware stored on a microcontroller. Although the fuse bits of the microcontroller may be set to write-only, the firmware and random data may leak (i.e. through software implementation errors, hardware errors, side channel attacks, etc.). In order to be immune against these attacks, the device does not "know" what the correct secret is. A given passphrase is used as a key for an extension function - it will extend the contents in any way, no matter what key is entered. A lost or stolen device will therefore give no information about the the owner's secrets to an attacker.
ATTACKS[Bearbeiten | Quelltext bearbeiten]
Tempest, Side-Channel & Power analysis[Bearbeiten | Quelltext bearbeiten]
This device may NOT be immune to side-channel attacks and has NOT been tested against tempest attacks. In fact, the communication over the USB Bus may well be captured by a tempest attacker. Protection agains this kind of attack can't be assured since this always depends on the configuration and hardware design of the host system.
This attack may also be viable on setups where a smartcard is used if the attacker is able to eavesdrop the communication between the operating system and the smartcard.
Overclocking[Bearbeiten | Quelltext bearbeiten]
An attacker that is able to overclock the microcontroller can lower the delay between two extension cycles and therefore may the be able to speed up brute force probing of the key.
Note: The attacker does not gain any knowledge about the secret stored on the dongle extension.
Replacing parts of the initrd[Bearbeiten | Quelltext bearbeiten]
The Initrd image on your harddrive needs software to send your passphrase to the usb device. This or other software within the initrd image on your system can be replaced by a malicious attacker. Usually this can be done by any user that has root privileges on your system.
Note: This attack is an essential problem with harddisk encryption nowadays. An attacker that is able to replace your bootloader, kernel, initrd or bios will be able to recover your encryption passphrase.
HARDWARE[Bearbeiten | Quelltext bearbeiten]
This device basically consists of an Atmega8 microcontroller, a push button and a dual-color (red/green) led. When the device is plugged in, it announces itself as an hid keyboard to the host system. When plugged it, it waits for a configurable amount of time before it accepts input from the host system (brute force & reset protection).
USAGE[Bearbeiten | Quelltext bearbeiten]
When plugged in, the device waits for the configured delay time and the red & green LEDs are blinking. When wait period is over, the green LED is blinking, signalling that the device is ready to receive commands. The device captures input from the host system as long as the push button has not been pressed. When pressed the input is fed to the extension function, processed and sent as "keystrokes" to the host system.
Diese Seite sollte verbessert/überarbeitet werden: Auf diese Seite wird nirgends verlinkt Über Verbesserungen an dieser Seite soll bei Bedarf auf der Diskussionsseite beraten werden Hier gelangst du zur Dokumentation dieses Banners. |